With the rising rate of data theft and increasing media attention given to hackers, malware, eavesdropping and, more recently, WikiLeaks, there is a greater awareness of the need for data security. Network administrators and end users alike are seeking ways to protect their data at home, and on their work and private networks.
The word data refers to the raw information that gets exchanged between users or computers. And while some people may still think that ‘data’ is what’s stored in databases, it can actually be anything from the personal files stored on your local computer to the email and other files that are transmitted within, and to and from, your organization.
One of the most important ways to protect the transmission of data from prying eyes is to use Secure Socket Layer communication, also known as Transport Layer Security: SSL/TLS.
How it works
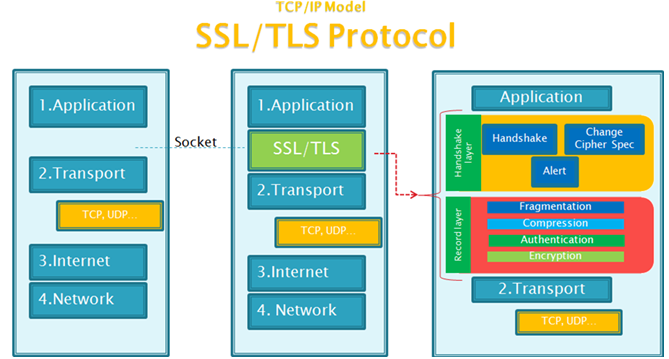
The SSL/TLS protocol functions between two layers of the OSI Presentation layer. The handshake and record layers operate over TCP/IP to encrypt data received directly from the Application layer.
SSL/TLS allows for mutual authentication (or handshake) between the mail client and server by sending information using the highest TLS protocol it can support: Certificate, Client Random Number (RN_C), Server Random Number (RN_S), a suggested list of Cipher Suites, compression method, Session ID (e.g., to resume an interrupted handshake), and so on.
The handshake data goes through a record layer which fragments, compresses and encrypts the data, which is then encapsulated in a TCP/IP packet to conform to the regular transmission model, and finally sent to its destination.
On the receiving end, the data goes through the reverse process of the same TCP/IP model: it gets decrypted, decompressed, and defragmented by the SSL/TLS protocol. It is then sent to the Application layer to finally be displayed on the user’s screen.
To use SSL/TLS, you must first look for a Certificate Provider, such as Entrust, VeriSign, DigiCert, etc., to make your Certificate Request (CSR). You will then be issued a certificate to install on your server, and thus begin encrypting your communications.



Thanks for the great explanation on SSL basics. People often use email in business and personal settings to send passwords, financial data, and other sensitive information without understanding all the risks and how easily their data can be hacked.